17 March 2023

Introduction
So far these articles have focussed on protecting your online accounts with effective password management. This time we are looking at how people can reach out to you directly to try and obtain your money or personal information.
Let’s get Wikipedia to define these terms for us:
-
Social Engineering: “…social engineering is the psychological manipulation of people into performing actions or divulging confidential information”
-
Phishing: “a form of social engineering where attackers deceive people into revealing sensitive information or installing malware such as ransomware”
- Ransomeware: is piece of malicious software that “threatens to publish the victim’s personal [or business] data, or permanently block access to it, unless a ransom is paid off”.
The distinction is sufficiently minor that we will refer to both these styles of attacks as “phishing”.
Phishing attacks can be delivered through a variety of means. For example:
- Phone calls
- SMS
- Online adverts
- Website popups
Many of the sites listed in the resources section below provide both general advice to help you and you should take some time to familiarise your self with the advice. This post can only cover so much.
Things to look out for
Phishing attacks can range from the crude to the very sophisticated, so it pays to be “hyper-vigilant”. They are crafted to appeal to our emotions and bypass our thinking brain. Some examples of these appeals:
-
Generosity and our natural desire to help people. For example by exploiting some current natural (or man-made) disaster, or reaching out to provide help to a specific individual which might even appear to be a close family member
-
Our fear or stress response, by suggesting that something bad will happen if we don’t perform some action quickly. These includes threats of financial loss, arrest, a security breach on our computer
-
Our trust of certain institutions, such as banks or governments
-
Wanting to get ahead in life or improve out financial security. Our desire to perform some beneficial action for ourselves
-
Our desire for human connection, for example via relationship scams
-
Our sense of fun or curiosity, by getting us to click on quizzes and other social posts
What are some of the “signals” to watch out for?
-
A caller claiming that you are about to prosecuted or fined. Remember the legal system does not work via phone calls or SMS messages
-
Someone claiming you PC is hacked and they can help you fix it. They might claim to work for a well know tech organisation like Microsoft
-
Any special deals that promise huge profits, something for nothing, or unbelievable bargains. Remember if it sounds too good to be true, then it invariably it’s not true
-
Unsolicited offers of a job
-
Claims that your bank account has been compromised. These scams are very good at crafting a message that immediately makes you feel anxious or fearful, if they sound plausible then always hang up and call the bank back on the number you know (not a number the caller gives you) to check.
-
Warnings or notifications about account renewal fees or parcels needing payment for collection
-
Someone unknown on reaching out looking to strike up a friendship or perhaps romance. It possible to form valid friendships online, but be very careful and prefer talking on public community forums instead of 1 to 1 messaging
-
Weblinks that don’t have the correct URL. Remember you can usually check the actually URL by moving your mouse over the link and looking for the address to appear (usually in a very small area in the bottom left of the screen). Sometimes the URL address looks very wrong, but often you have to careful, as in this example.
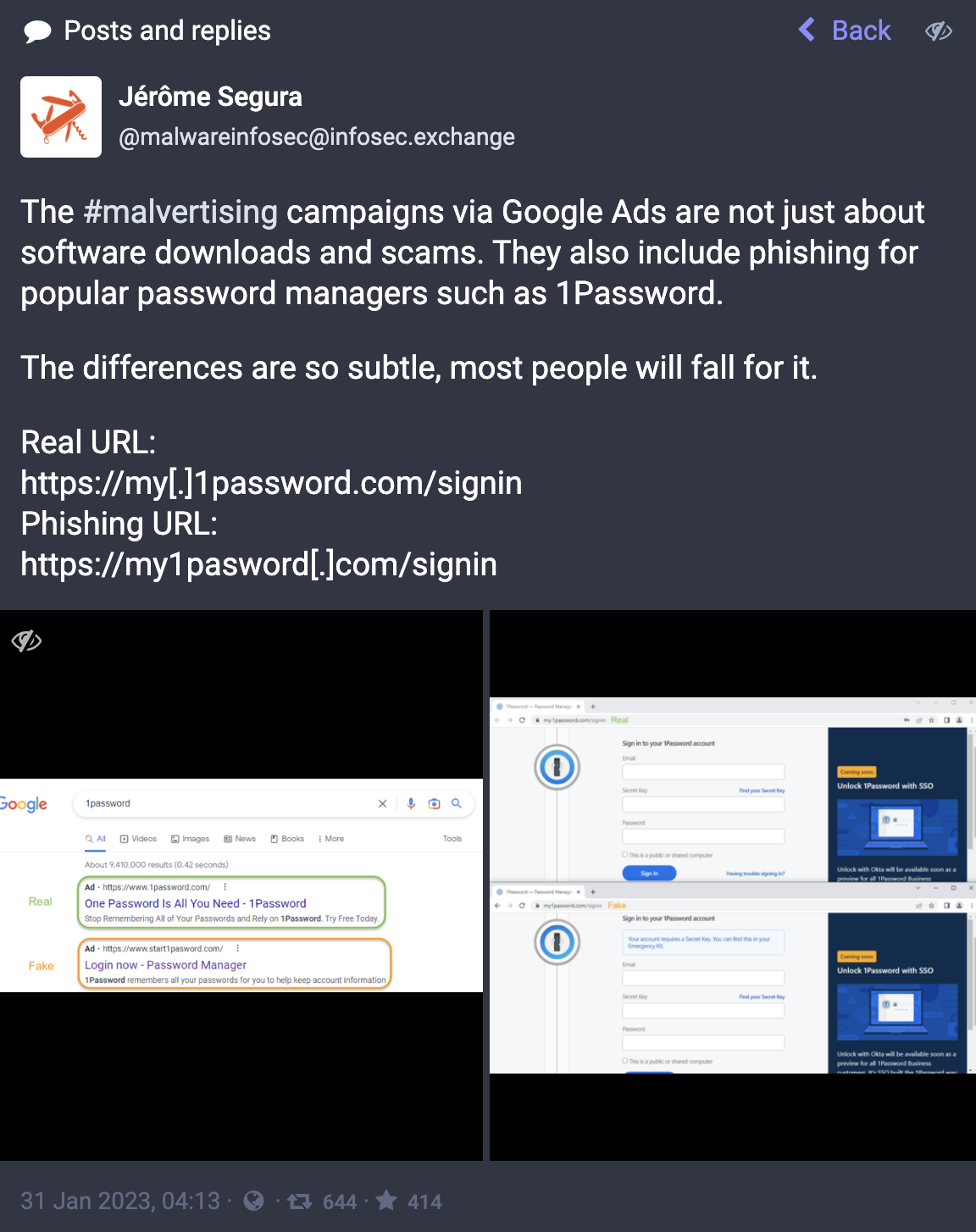
Jérôme Segura on Mastodon
Other Resources
- Australia and New Zealand’s national identity and cyber support service
- Federal Government e-safety library
- Safety@Facebook
- Google Security Tools and tips
- Top tips for staying secure online by UK Government
- The Best Two-Factor Authentication App NY Times
- Two-Factor Authentication: Keeping Your Accounts Secure
- Time to Kill Security Questions—or Answer Them With Lies | WIRED
- Twitter is ending free SMS two-factor authentication. So what can you use instead?
About the writer
Alec has been in IT for over 40 years and using the Internet since the 1990’s. He has an active online presence and uses Google, Mastodon, and LinkedIn (amongst many others). You can find more about him by Googling “alecthegeek”, or looking at his website (which does have a padlock symbol). He does not claim to be a security expert.
This work is licenced under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License.

